

Top 3 Ways to Protect Your Veeam Backup Data from Ransomware
This topic comes up time and again when meeting with customers. With the average attack costing over $36,000 and it seeming like hospitals, cities, and schools are constant targets, it's no wonder the threat of ransomware is top of mind.
While there are many strategies for protecting your Veeam backup data from ransomware, here are three of the most effective:
1. Keep Backup Repositories Off Domain
This prevents a compromised domain account from encrypting data stored on the repository. Instead, use local accounts which are exclusively used by Veeam for the purpose of connecting to the repository.
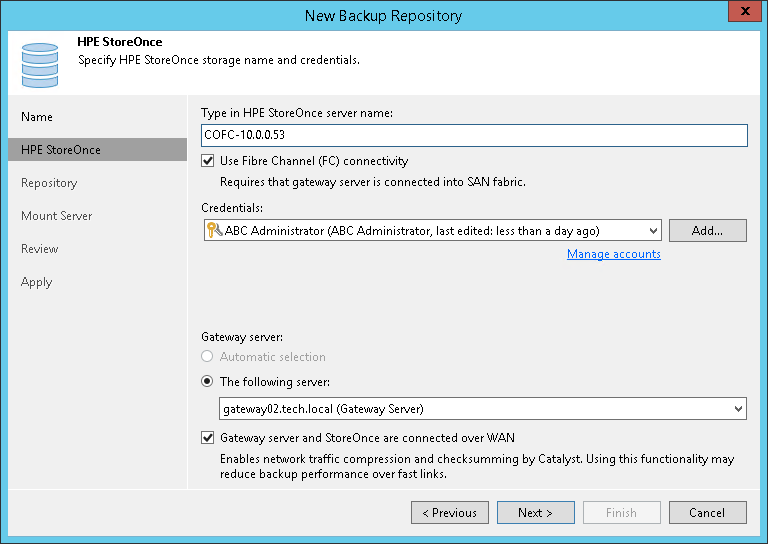
2. Copy Backup Data to a Dedicated Appliance via Proprietary Protocol
In addition to a compromised system having local data encrypted, ransomware payloads are known to encrypt data in shared folders which are made available over the network via common protocols (SMB/CIFS, NFS). By using a proprietary protocol, such as, HPE StoreOnce Catalyst, we can greatly reduce the likelihood of a compromised account being able to access and encrypt the data stored on a dedicated backup appliance.
3. Leverage Veeam Cloud Connect and/or Cloud Tier for Out of Band Storage
If you’re reading this, chances are you're familiar with the 3-2-1 backup strategy. Having backup data offsite is an important part of being able to effectively recover from various disaster scenarios.
Veeam offers a couple options for getting backup data offsite: Cloud Connect and Cloud Tier.
Veeam Cloud Connect allows backup and replication jobs to target a service provider, which enables cloud-based disaster recovery.
Veeam Cloud Tier allows backup data older than a defined age to be moved to object storage – on-prem or off.
FURTHER READING
- Top 10 Ransomware Stories of 2019
- How to protect your data from ransomware and encryption Trojans
- 7 Practical tips to prevent ransomware attacks on backup storage

